Crime is paying less often for cyber hackers as improved corporate security measures — and dramatically higher ransom demands — sway more companies to reject extortion payments for seized data, according to a report on cybersecurity.
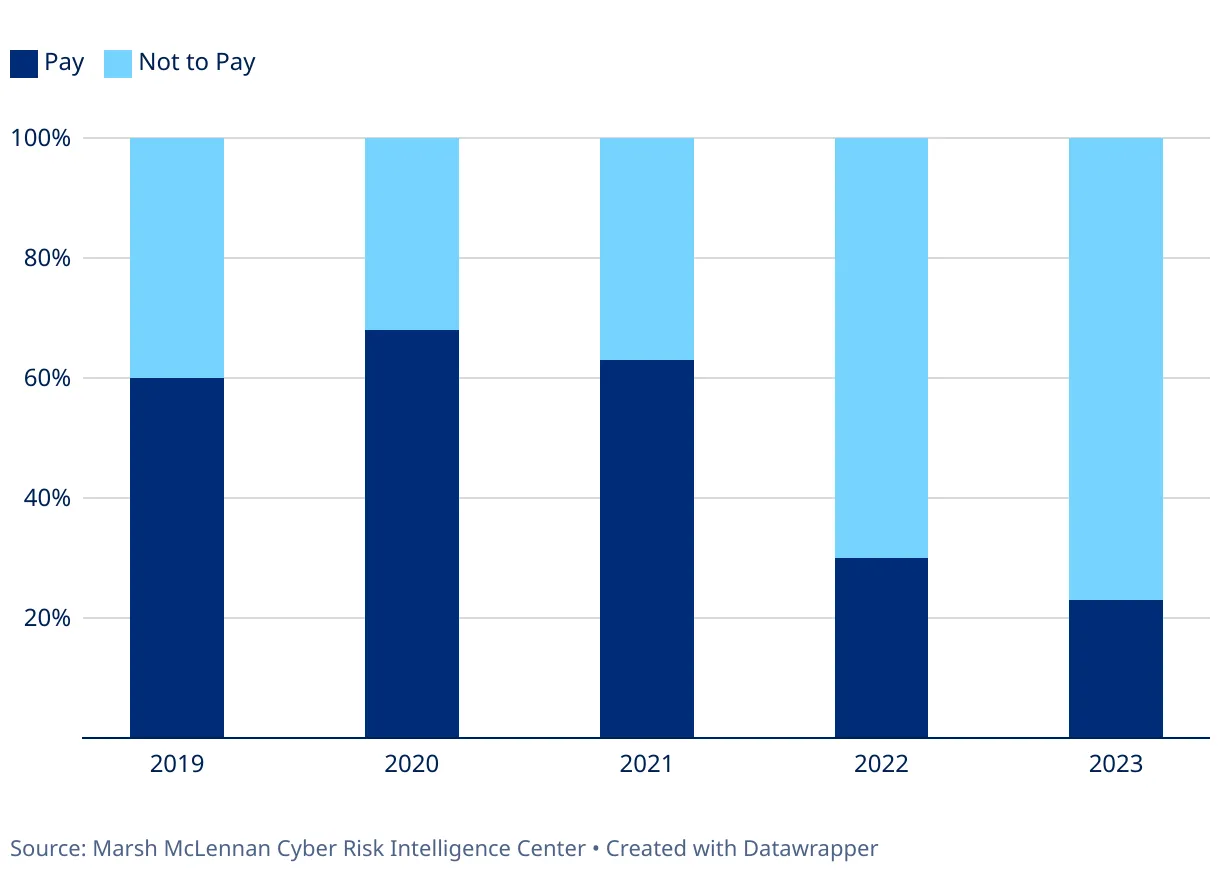
Less than a quarter of companies insured by Marsh, or 23%, paid ransom demands last year, despite a 64% jump in extortion events from 2022 to a record 282, the insurance broker and risk advisor said in a June 11 report. In 2021, Marsh noted, 63% of its clients paid an extortion demand to protect data.
A ransomware attack is one in which hackers misappropriate and encrypt sensitive data with the threat of keeping it hostage or releasing it publicly unless a ransom is paid.
Companies, especially larger ones, are “just more resilient than they were three, four, five years ago,” Meredith Schnur, managing director of Marsh’s U.S. and Canada cyber practice, told Legal Dive on June 13. Executives overseeing legal, risk, technology and privacy areas have also grown more sophisticated in their approach to mitigating the effects of hacks relative to just five years ago, she said.
More extorted companies are declining to pay attackers
When ransomware “initially reared its ugly head,” attacks were “very fast and furious,” Schnur said. “Companies weren’t ready. The threats were, ‘We're gonna lock it and you’ll stay locked down.’ And they were very potent,” she said. “It was (data is) locked down, you can't move, or you need to get the decryption key, because we have all your data, and we’re going to release it. And it was very scary.”
Today, a company struck by a ransomware intrusion may find that the resiliency measures engineered by its legal, risk, information security and technology departments are suitable to a point that the business isn’t fully impaired. And that can directly affect a company’s decision to pay ransom.
“With better resiliency, better maturation, you're not necessarily locked down,” Schnur said. “I might be a little bit handicapped at operating, but I can still operate on the data front.”
Surging ransom demands
The median ransom demand soared to $20 million last year from $1.4 million, according to the report, which analyzed more than 1,800 U.S. and Canadian cyber claims Marsh processed in 2023. That yearly claims total was a record, although ransomware attacks represented less than one-fifth of all corporate cyber attacks, relative to data breaches, theft and other hacks.
“Every situation is unique, and a decision to pay or not to pay a ransom can have consequences beyond the specific incident at hand,” the report states.
Globally, ransomware victims paid a record $1.1 billion in 2023, the first year extortion payments topped $1 billion, according to Chainalysis, a blockchain data research and services company.
Another factor in the decision about whether to meet a ransom demand: Many malicious cyber actors are based in Russia, a target of financial sanctions from the U.S. and Europe over the 2022 invasion of Ukraine. The sanctions regime creates legal issues for many U.S. and Canadian companies, precluding payments to entities in a sanctioned country, Schnur said.
Global scourge
Ransomware attacks have become frequent, around the world.
In early June, a cyber assault on a blood-testing provider for the UK’s National Health Service created operational chaos at London-area hospitals. An attack the following week on the IT systems for Traverse City, Michigan, and the surrounding county, disrupted some municipal services and halted court proceedings.
These cyber crimes also rank among companies’ top risks – a lengthy list of concerns that includes terrorism, extreme weather events and labor shortages. In a 2023-2024 perception survey by the World Economic Forum that ranked the estimated impacts of 34 global risks, “cyber insecurity” was the fourth-highest corporate concern over the next two years and eighth over the next decade.
Shifting the risk
Even as law enforcement becomes more adept at pursuing cybercriminals — this year an eight-nation international effort snared the most prolific group, Lockbit — companies are increasingly likely to transfer their cyber risks to insurers, Schnur said.
The healthcare industry remains ransomware hackers’ top target, owing to its rich abundance of sensitive patient data, the severity of regulations governing such data and the heightened threat that medical devices critical to life can be compromised, according to the report.
“The more resilient that companies find themselves, and the more the culture around cyber maturation and their journey just gets better and better and better, you can see less payments and then the ransom,” Schnur said